BitBox 02.2024 Fletschhorn update
BitBox 02.2024 Fletschhorn update
Architecture
The BitBox02 hardware wallet is a USB device which securely stores cryptographic keys (such as bitcoin private keys) and signs transactions/messages with that key. Signing with the key requires physical interaction with the device (i.e. no automatic or remote signing possible). The BitBoxApp is the native app that communicates with the BitBox02. However the BitBox02 can integrate with various third party applications. It can communicate with applications running in a browser (or browser extensions) using WebHID or using the BitBoxBridge. The BitBox02 can also communicate with third-party bitcoin wallets using the Bitcoin Hardware Wallet Interface (HWI).
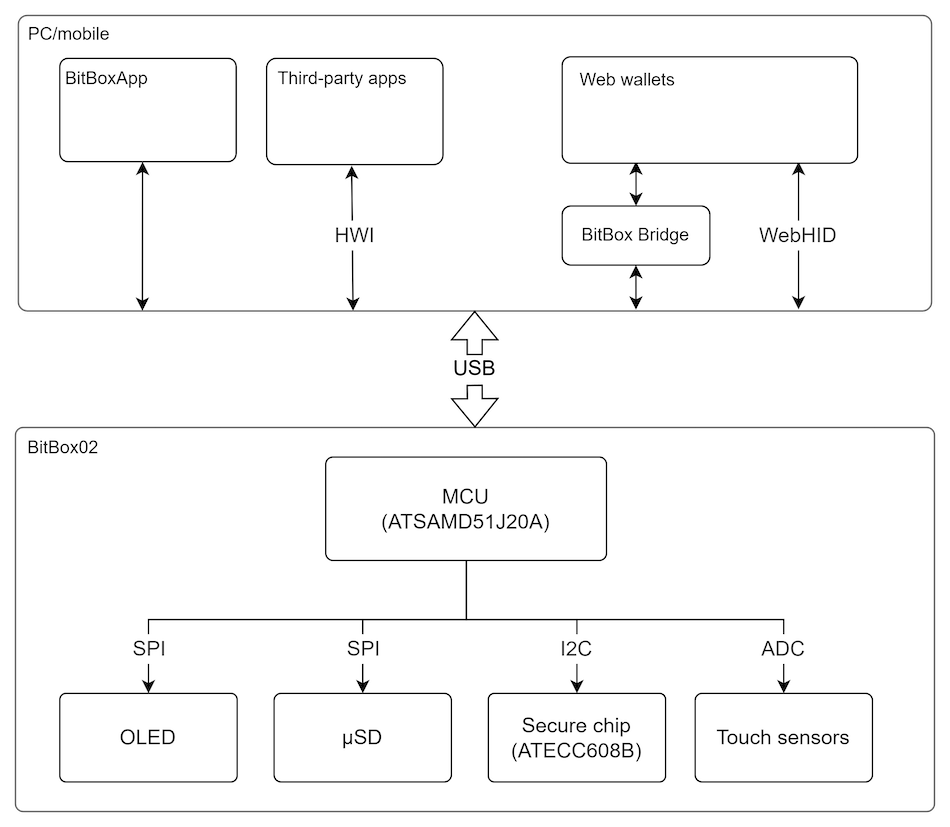
The main components of the BitBox02 are:
OLED display: displays important information to the user. Such as bitcoin transaction details or a private key.
microSD card connector: used to backup private keys onto a microSD card.
Touch sensors: Used to interact with the device. Interaction with the device is required for important tasks, such as signing a bitcoin transaction.
Secure chip (ATECC608B): hardens the user-chosen password by combining it with a key stored on the secure chip. Also limits the number of key derivations using a monotonic counter enforced by the secure chip.
Microcontoller (ATSAMD51J20A): runs the open source firmware of the BitBox02 and communicates with the other on-board components.